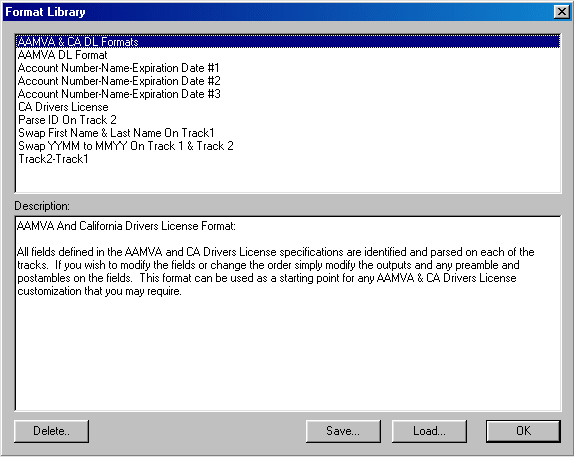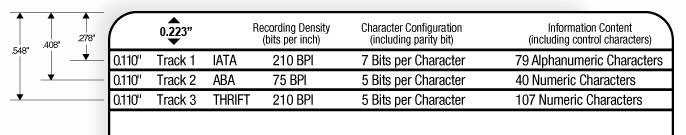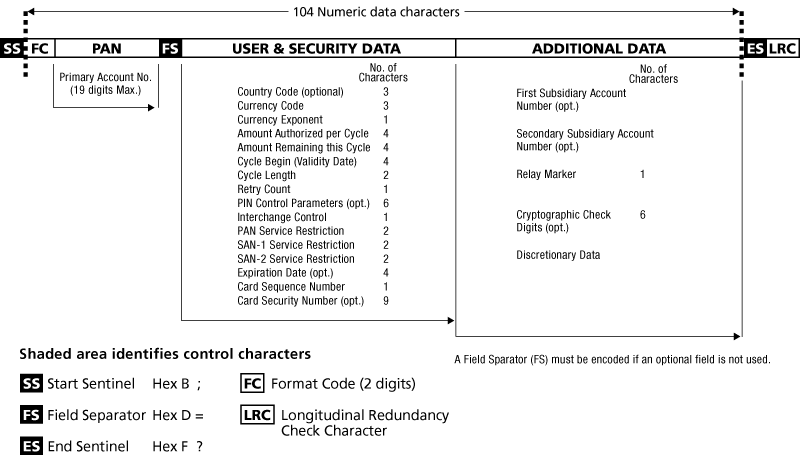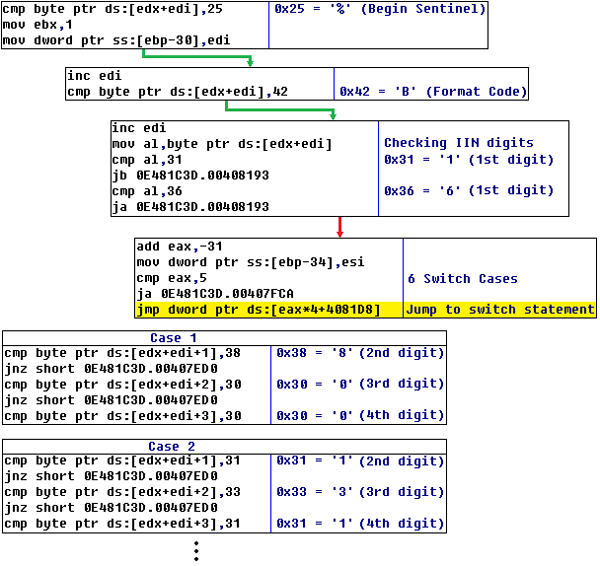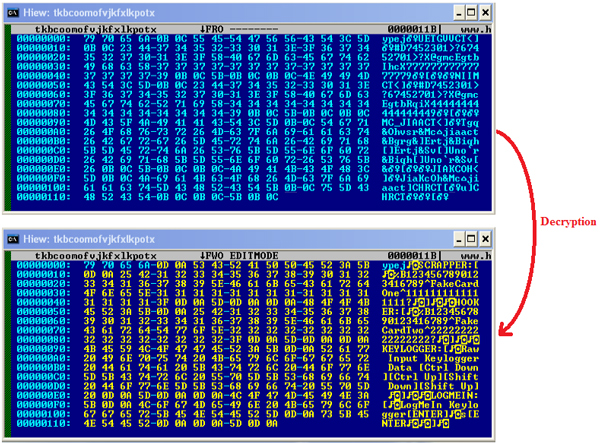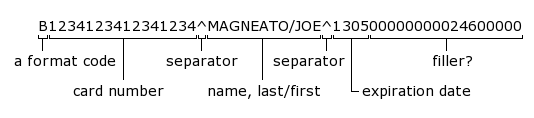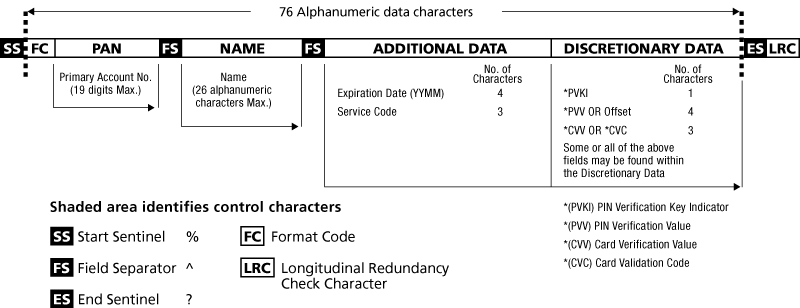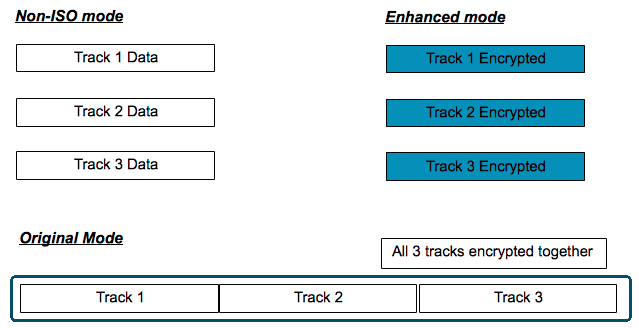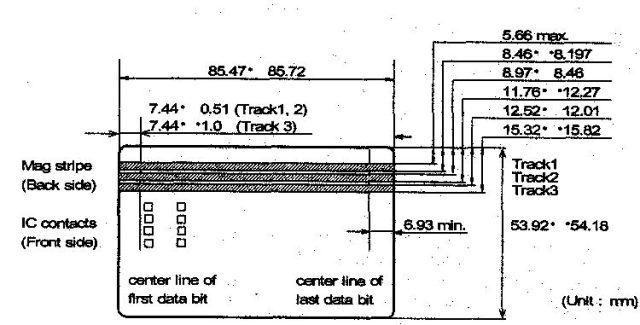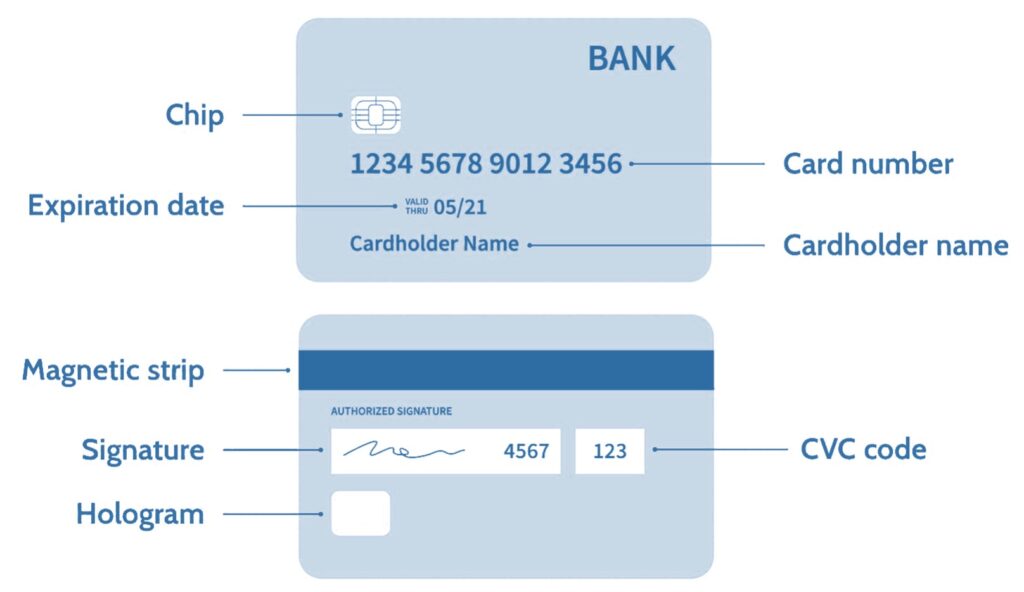
What is Track 1, 2, and 3 Data in Magnetic Stripe Credit Cards? - Credit Card Processing and Merchant Account

What is Track 1, 2, and 3 Data in Magnetic Stripe Credit Cards? - Credit Card Processing and Merchant Account
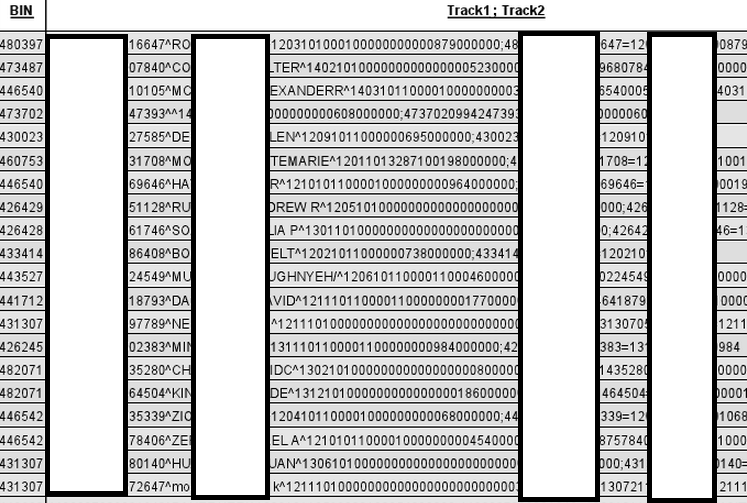
Cybercriminals entice potential cybercriminals into purchasing bogus credit cards data - Webroot Blog