SHA-256 Animation' that allows you to intuitively understand the calculation process of the hash function 'SHA-256' with animation - GIGAZINE

Contents of the padding+length field for SHA-256 2 (a), and SHA-256 3 (b) | Download Scientific Diagram

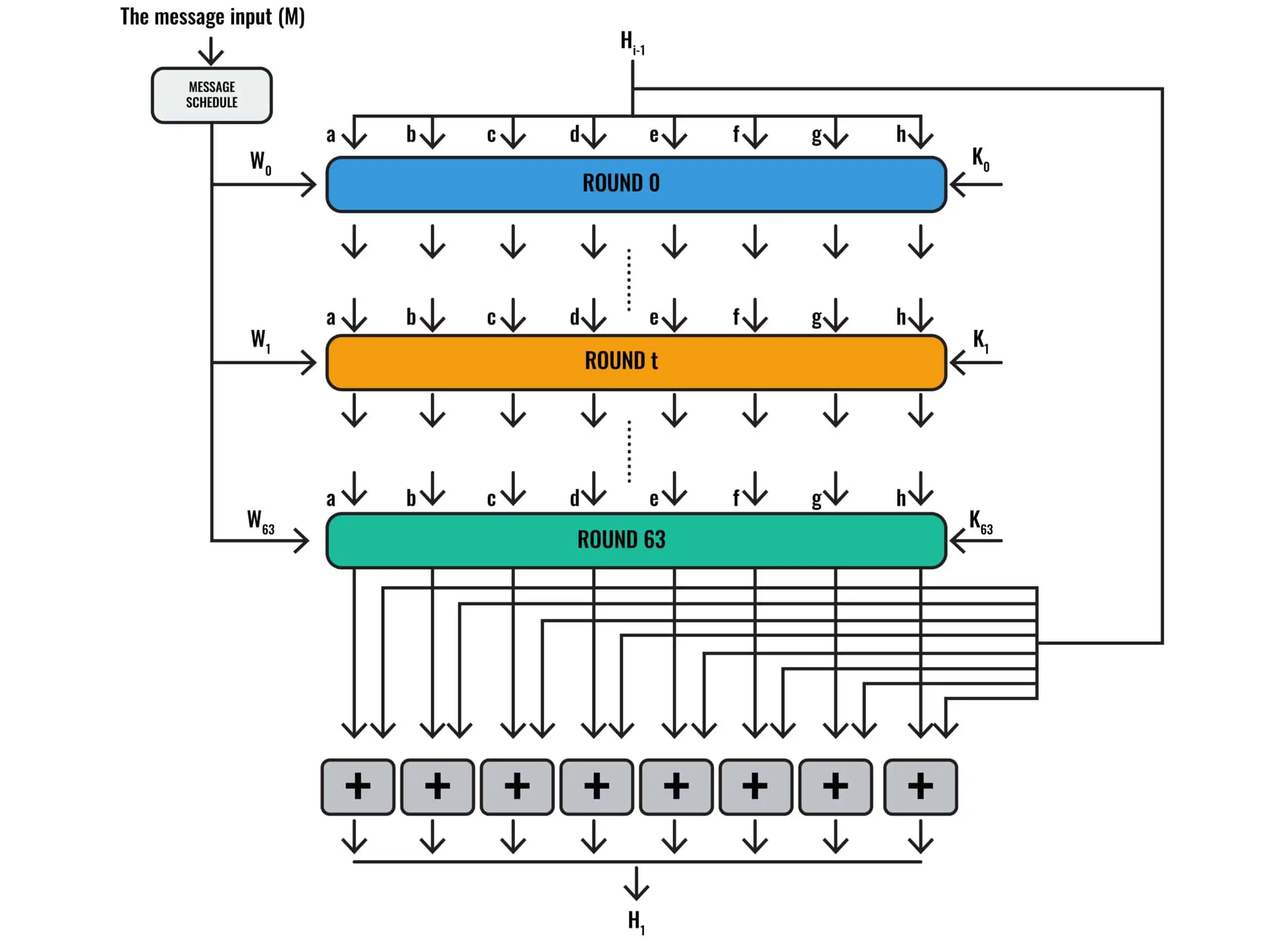
Figure 10 from Optimising the SHA256 Hashing Algorithm for Faster and More Efficient Bitcoin Mining 1 | Semantic Scholar

The internals of SHA-256 when hashing a 640-bit message as used in the... | Download Scientific Diagram

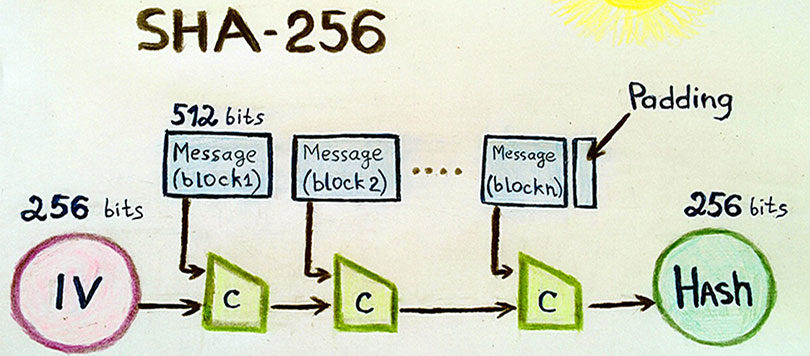
Message preprocessing: padding c. Definitions In the SHA-256 algorithm,... | Download Scientific Diagram
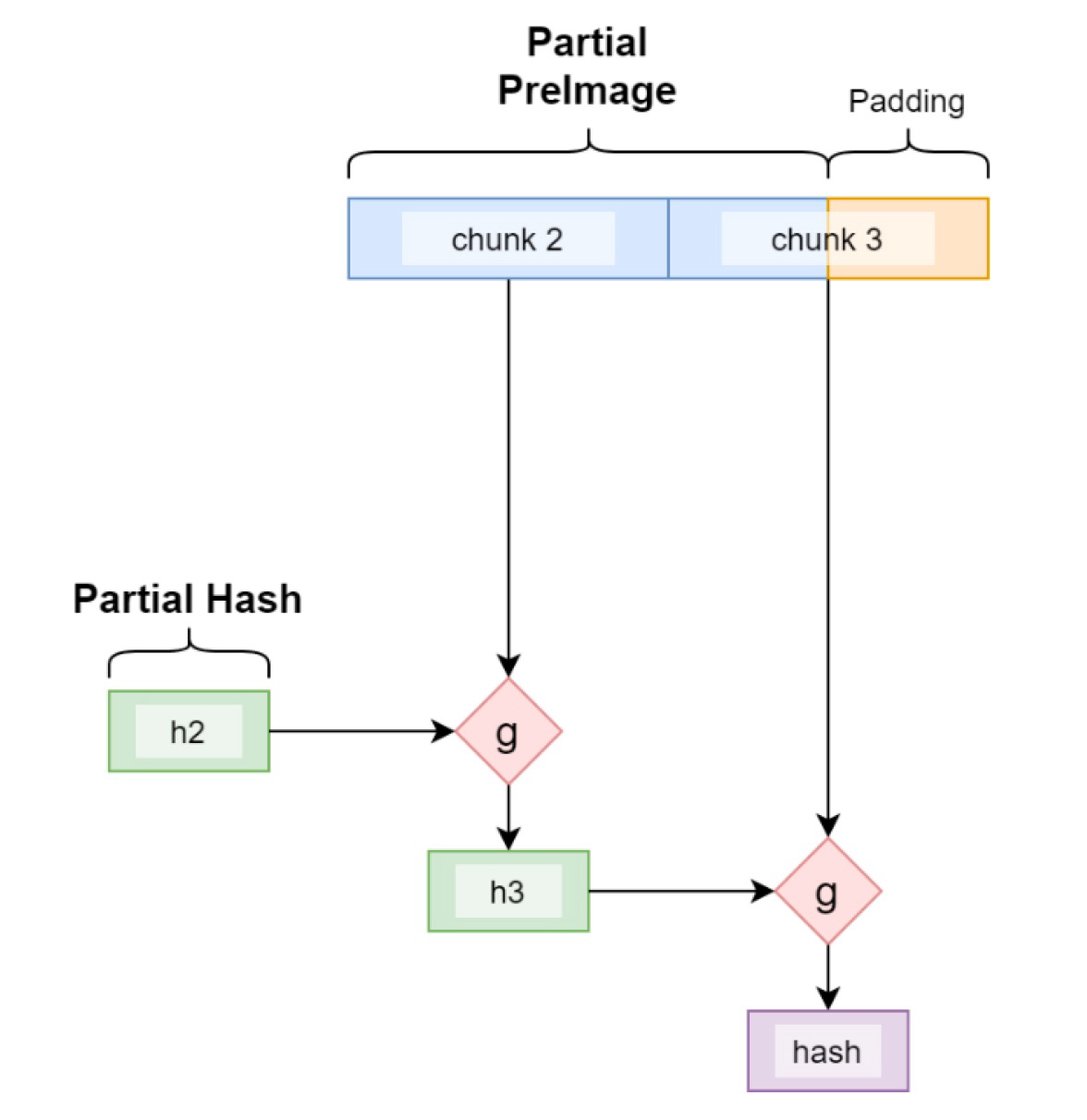
The Partial Preimage Technique. How to Use Length Extension Attacks For… | by sCrypt | Coinmonks | Medium